diff options
| author | Emiliano Ciavatta | 2020-10-20 15:45:18 +0000 |
|---|---|---|
| committer | Emiliano Ciavatta | 2020-10-20 15:45:18 +0000 |
| commit | e4b73c0c3ce2c8817ddd1b8cfaa672823b59a422 (patch) | |
| tree | 105e92d231a6c3c8759b0eab4d326de2b36221bf /README.md | |
| parent | 0c13228651cb298194a5d97615e74f5fc7749fdc (diff) | |
| parent | cf062076f238d97d6d01fe6e542b5f8c77a624ba (diff) | |
Merge branch 'develop' into main
Diffstat (limited to 'README.md')
| -rw-r--r-- | README.md | 40 |
1 files changed, 24 insertions, 16 deletions
@@ -1,6 +1,7 @@ # `caronte$` [](https://travis-ci.com/eciavatta/caronte) +[](https://hub.docker.com/r/eciavatta/caronte) [](https://codecov.io/gh/eciavatta/caronte) [](https://www.codacy.com/manual/eciavatta/caronte?utm_source=github.com&utm_medium=referral&utm_content=eciavatta/caronte&utm_campaign=Badge_Grade)  @@ -15,21 +16,28 @@ The connection flows are saved into a database and can be visualized with the we ## Features - immediate installation with docker-compose - no configuration file, settings can be changed via GUI or API -- the pcaps to be analyzed can be loaded via `curl`, either locally or remotely, or via the GUI +- pcaps to be analyzed can be loaded via `curl`, either locally or remotely, or via the GUI - it is also possible to download the pcaps from the GUI and see all the analysis statistics for each pcap - rules can be created to identify connections that contain certain strings - pattern matching is done through regular expressions (regex) - regex in UTF-8 and Unicode format are also supported - - it is possible to add an additional filter to the connections identified through pattern matching by type of connection -- the connections can be labeled by type of service, identified by the port number +- connections can be labeled by type of service, identified by the port number - each service can be assigned a different color -- it is possible to filter connections by addresses, ports, dimensions, time, duration, matched rules -- supports both IPv4 and IPv6 addresses - - if more addresses are assigned to the vulnerable machine to be defended, a CIDR address can be used +- ability to filter connections by addresses, ports, dimensions, time, duration, matched rules +- a timeline shows statistics with different metrics sampled per minute + - some of these metrics are *connections_per_service*, *client_bytes_per_service*, *server_bytes_per_service*, *duration_per service*, *matched_rules* + - with *matched_rules* metric it can be possible to see the relationship between *flag_in* and *flag_out* + - the timeline contains a sliding window which can be used to search for connections in a certain time interval +- advanced search by term, negated term, exact phrase, regex, negated regex + - the performed searches are saved to be instantly repeated the following times - the detected HTTP connections are automatically reconstructed - HTTP requests can be replicated through `curl`, `fetch` and `python requests` - - compressed HTTP responses (gzip/deflate) are automatically decompressed -- it is possible to export and view the content of connections in various formats, including hex and base64 + - compressed HTTP responses (gzip/deflate) are automatically decompressed +- ability to export and view the content of connections in various formats, including hex and base64 +- JSON content is displayed in a JSON tree viewer, HTML code can be rendered in a separate window +- occurrences of matched rules are highlighted in the connection content view +- supports both IPv4 and IPv6 addresses + - if more addresses are assigned to the vulnerable machine to be defended, a CIDR address can be used ## Installation There are two ways to install Caronte: @@ -77,17 +85,17 @@ The backend, written in Go language, it is designed as a service. It exposes RES ## Screenshots Below there are some screenshots showing the main features of the tool. -### Viewing the contents of a connection - +### Main window, with connections list and stream content +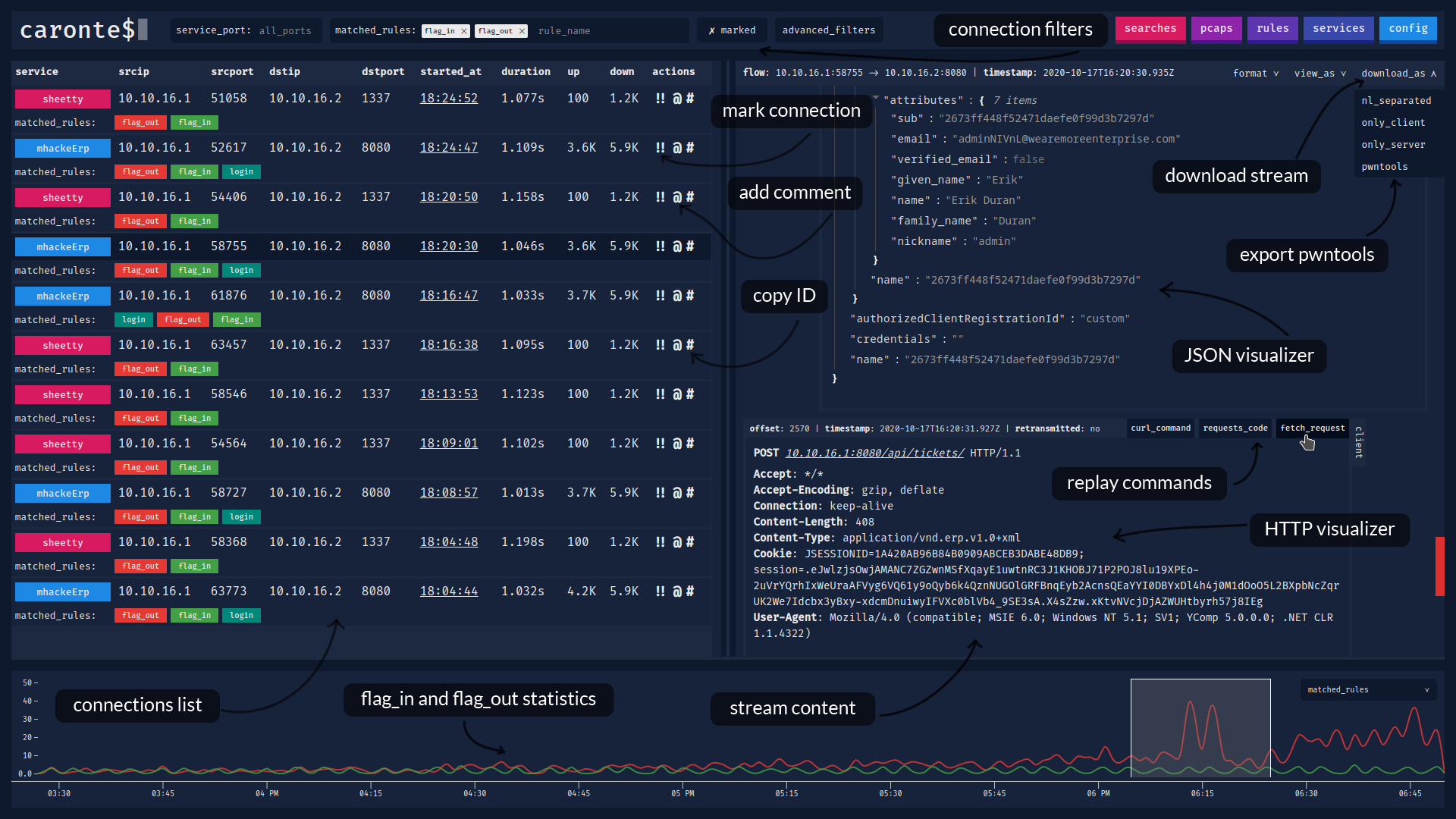 -### Loading pcaps and analysis details - +### Main window, with the timeline expanded +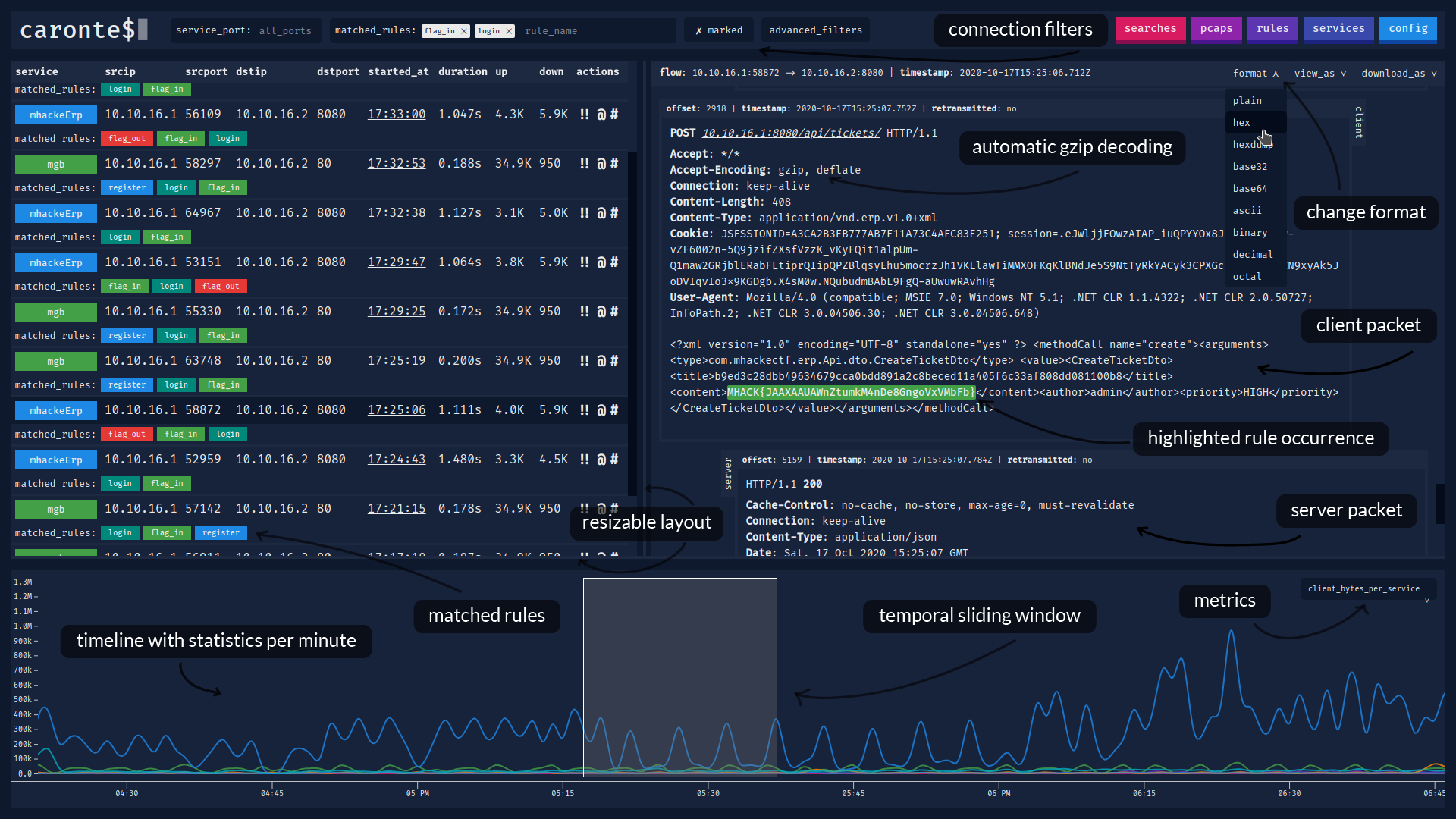 -### Creating new pattern matching rules - +### Rules and services view +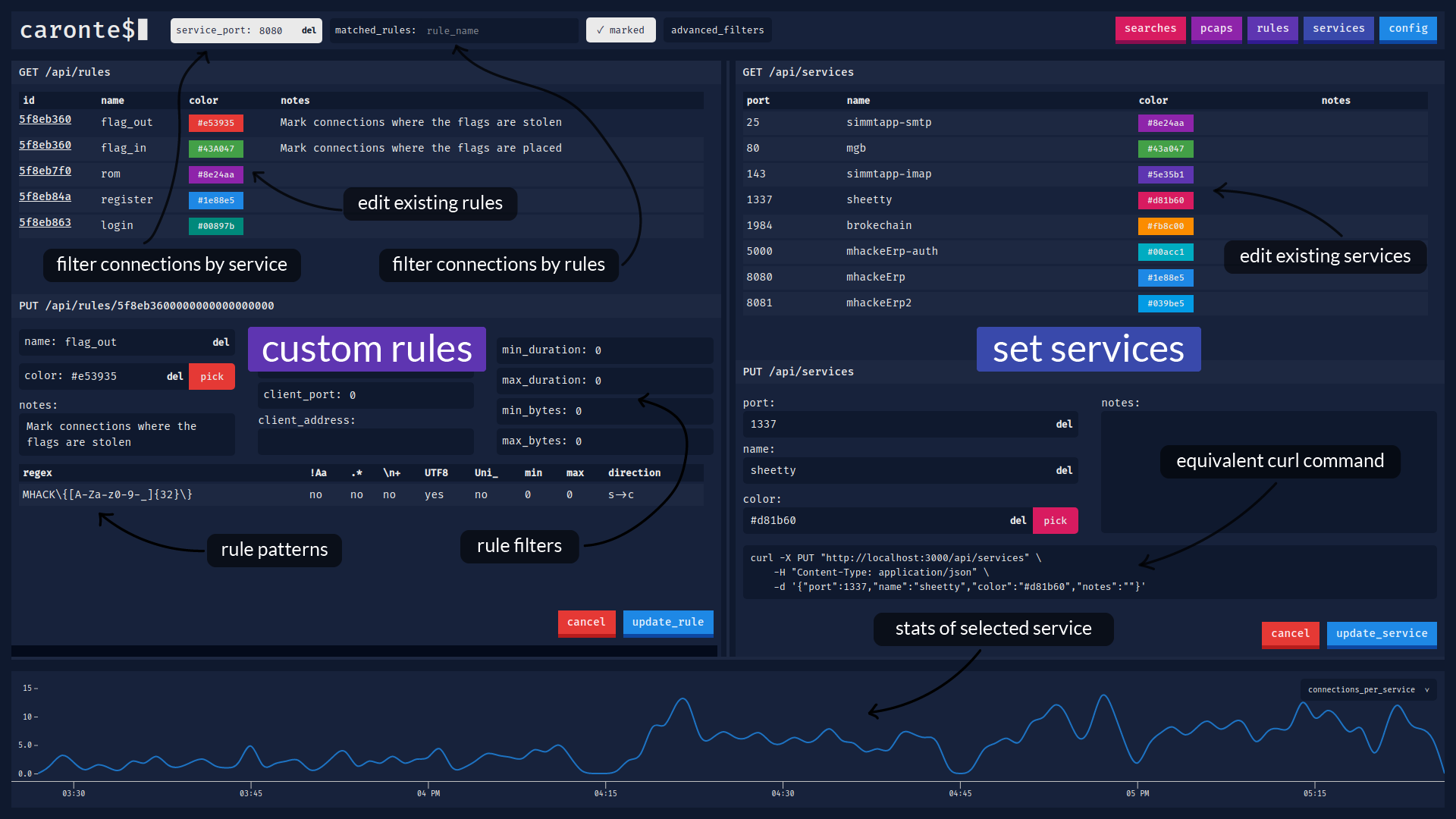 -### Creating or editing services - +### Searches and pcaps view +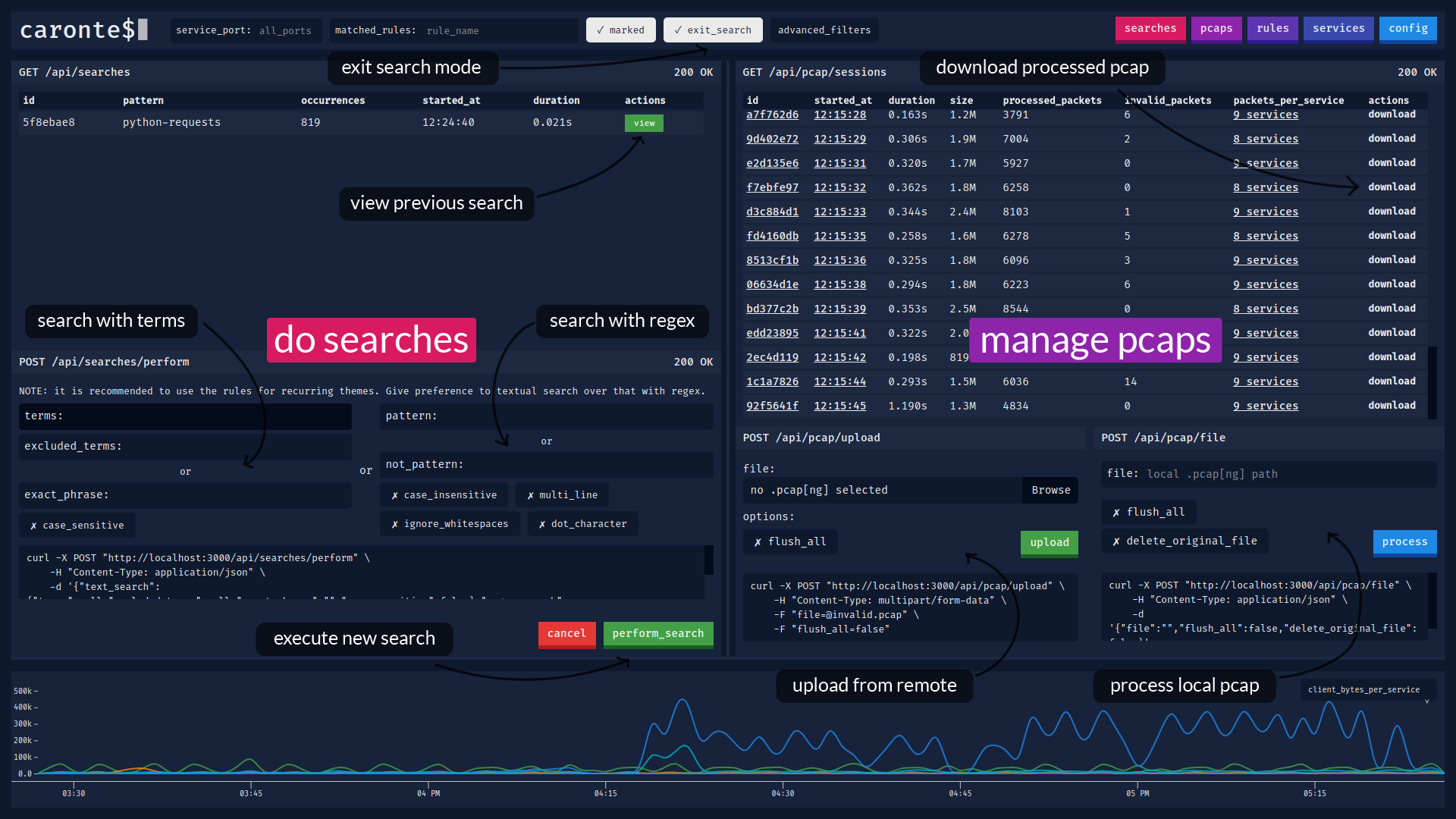 ## License caronte was created by [Emiliano Ciavatta](https://eciavatta.it) and is licensed under the [GPL-3.0 license](LICENSE). |
